You can just enter anydesk then once the client is launched enter the id and password of machine which you want to connect to. Here is a list of the available command if you want to stay on the command prompt https://support.anydesk.com/CommandLineInterface. Discover AnyDesk, the secure & intuitive remote desktop software, and take advantage of the application's innovative features! Call Sales: +49 711 217 246 705 Get Help. In this video, I'm going to show you 'How To Setup #Unattended Access Password in #AnyDesk'Make sure to check out my other Important tutorials. Any Desk is a great tool whenever it's necessary to realize remote connection to a PC. It is very simple to use and the interface is easy to understand.
What Is Remote Desktop?
A co-worker asks to see something on your screen, but you’re in a different room.
A friend from a different country has a problem with their device, and you need a quick and simple way to help.
You work for a large company and are looking for a way to roll out software on all devices.
These and many other use cases are what remote desktop is for. It allows you to remotely access another computer over the internet from wherever you are in the world. Ideally, this works across all platforms: from your Android phone to your Linux computer, from Windows to Mac.
AnyDesk offers one of the simplest remote access solutions. Don’t believe us? Try it out for yourself! Here’s a little guide on how to remotely access another computer over the internet via AnyDesk.
1. How To Download AnyDesk
First things first: AnyDesk is free for private use. So if a family member needs help setting up their PC, you can comfortably help them from home and you don’t have to pay a cent. Not only that, but you don’t have to sign up for anything, and you barely need any space on your PC. Simply download the 3MB file and get going!
Whoever you’d like to connect to needs to download AnyDesk as well. Just tell them how easy it is, and they’ll be ready in moments. And that’s it! You’re now ready to start your first session.
2. How To Set up a Connection
To get started, open AnyDesk. The number you see on the left is your personal ID. People can use this number to access your device, and you need this number from the person you want to connect to. Type the ID of the remote device into the search bar on the right. Don’t forget: Never give anyone you don’t know access to your device and beware of online scammers!
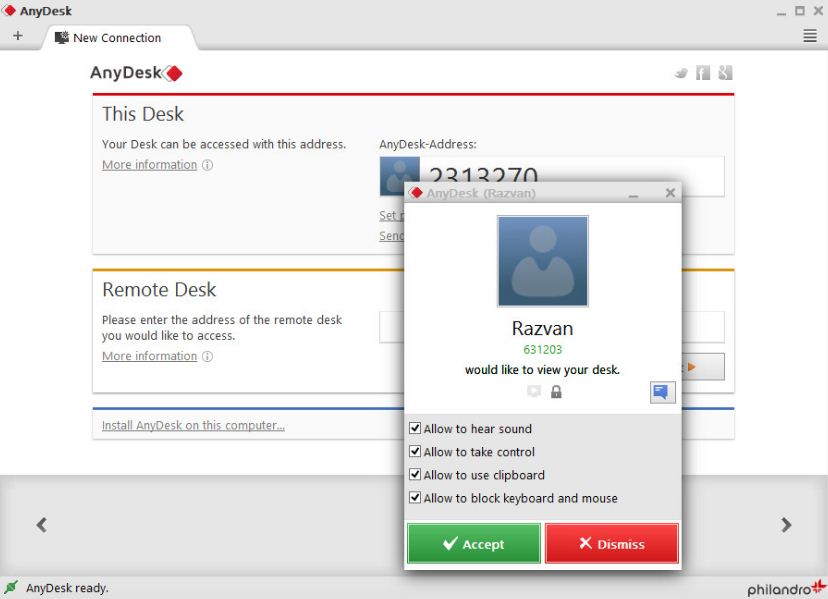
What if you’re at home, but you want to have unattended access your work PC at the office, where no one is there to accept the session request? Take a look at your security settings: There you can set up a password and two-factor authentication for unattended access. That way, the session doesn’t need to be manually accepted by the remote side.
How else can you choose who to connect to? When you open the AnyDesk home window, possible contacts and their online status are displayed as follows:
- DISCOVERED: This where the devices that have AnyDesk installed and are part of your network are listed.
- FAVORITES: Your most-accessed devices are listed here.
- RECENT SESSIONS: The devices you recently connected to are listed here.
Want to organize your contacts even further? Our AnyDesk Performance license contains an Address Book among many other helpful features, where you can categorize your contacts via tags.
3. How To Use AnyDesk’s Remote Desktop Features
On the remote side, as soon as a session is requested, the accept window pops up. You may take control of the remote device, but the remote side can still decide the level of control they want to give you by simply clicking the respective permissions on the accept window. For example, the On-Screen Whiteboard can be disabled, as well as the clipboard, file manager and even the ability to use mouse and keyboard of the remote side.
Depending on the permissions, here’s a selection of tools you can use during your remote session:
- Chat: This is the simplest way to communicate with the remote side via AnyDesk.
- On-Screen Whiteboard: Need to visualize something on screen? Draw sketches or arrows in multiple colors.
- Switch Sides: The remote side wants to have access to your device? You don’t need to end the session and start a new one—just switch sides in the active session.
- Block User Input: This blocks the user on the remote side from controlling their device. That’s so you don’t get in each other’s way, and the user on the remote side can lean back while you help them.
To end the connection, either click disconnect on the remote side, close the tab or close AnyDesk.
Easy, isn’t it? These first steps aren’t even half of what AnyDesk is capable of. Find out more about AnyDesk Remote Desktop and if you need advanced functions that are tailored to your needs, consider buying one of our licenses.
Social engineering means evoking a reaction,oftentimes an emotional one, and using it to trick a victim into taking actionor disclosing information. Usually, fraudsters use manipulation and try toevoke curiosity and a sense of urgency in their victims. Their goal is to gainaccess to personal or bank accounts or to install ransomware on your device todemand payments.
Unfortunately, these types of attacks have many names and faces, so there is no one way to avoid them (except for a heightened sense of caution). These scams can be encountered everywhere: online and offline. You can get instant messages, e-mails, phone calls, pop-ups, or links. Thankfully, there are certain clues that you can look out for. As a general rule, always remember that if it sounds too good to be true, it probably is. Here are some examples of scam tactics and how to deal with them.
“Log into your bank account now!”
If you have an e-mail account, chances areyou’ve been a victim of phishing. Preying on fear, scammers will send messagesfrom a seemingly trusted source urging action. The typical example is an e-mailfrom your bank: If you don’t log into your account now, it will be terminated!You will be fined! You get worried because the mail seems legitimate by thee-mail address and the layout. Even the link looks to be real. By triggeringurgency, fraudsters want you to act before you think and give away your databefore you can reflect on the legitimacy of the mail.
“You won!”
You get a message telling you that you wonan iPhone or an e-mail that you inherited money from a distant relative thatyou didn’t even know. This method is designed to capture your attention; tomake you curious. Even if you don’t believe it, maybe you’ll still click on thelink just because there’s a glimmer of hope that it’s true.
We’re sorry to inform you that it isn’treal.
“You have a problem with your PC? We willhelp for free!”
Getting this type of message can beconfusing. You didn’t ask for IT support, especially not from this company. Butthen you think to yourself: I actually do have some problems with my PC. And ifI don’t have to pay for it – what could go wrong?
The answer is a lot. They could ask you toinstall a program while disabling your antivirus program and before you knowit, you allowed malware disguised as a software update onto your device.
Sadly, companies don’t actually reach out topotential customers and offer help for free.
“Hello friend. You have to check thisout!”
Even when you get an e-mail from a personyou trust, you’re not necessarily safe from scammers. E-mail accounts can behacked and used to spam their contacts. This can include links that you just have to check out. Or, again,preying on trust and fear the scammers can pretend to be a friend who is indanger: Maybe they have been arrested and need bail, maybe they’re at thehospital… Again, the fraudster wants you to act before you think and give awaypersonal data. This could also come in the form of a phone call. We are morelikely to not think and just click on the link when it’s from a source wetypically trust.
“Get the new movie for free!”
You might have seen a message like thisdisplayed on a website. Maybe there’s even a little animation to capture yourattention. If you want free malware, download this file. We’re afraid you won’tget the latest blockbusters, though.
What to do now:
All of these scenarios can be dealt with inthe same way: Be careful!
If you’re asked to download or install anything, don’t do it. If you’re asked to log in and fill in your bank account data, don’t do it. Avoid clicking on links and don’t open attachments. When in doubt, simply call the company to ask about the legitimacy of the mail. Nothing is ever so urgent that you can’t make a quick phone call.
Get Anydesk For Windows
Scammers are counting on their victims acting rashly. Better you question the message one too many times. Check the source, and then check it again. You could also research the wording of the suspicious mail. Usually, you will quickly find fellow victims and their tips on how to react.
Is Anydesk A Scam
Make sure you have the latest version of a reliable antivirus program. Also, e-mail software usually filters out spam mail. In most cases, these filters can be trusted and you can change the settings to make them more strict. Now, as long as you stay calm and question every suspicious e-mail you get, you and your data should be safe from all different types of social engineering attacks.
